In what cybersecurity experts are calling the largest leak of its kind, over 16 billion stolen login credentials—including usernames, passwords, and authentication tokens—have recently surfaced on the dark web.
The breach contained data gathered from over 30 separate leaks, and reportedly, is the result of widespread infostealer malware rather than the failure of any single platform. Regardless, it affected users of major online service providers like Google, Facebook, and Apple, posing a serious threat to individuals and businesses alike.
This isn’t just another recycled password dump. Researchers believe that the data is recent, valid, and likely exploitable. This could have catastrophic consequences, such as hijacking, fraud, and identity theft at an unprecedented scale.
In this post, we’ll break down what exactly happened, what it means for your data security, and most importantly, what steps you could take to protect yourself in the wake of this massive breach. We’ll discuss how to practice strong password hygiene and reduce your reliance on cloud-stored credentials, and we’ll also explore hardware-encrypted tools like SecureUSB and SecureDrive that can give you a secure, physical alternative to manage your most important data.
Let’s dive into it.
What Actually Happened?
In June, cybersecurity researchers uncovered a massive compilation of user credentials, reportedly including over 16 billion usernames, passwords, and session tokens. This data breach is widely believed to be the largest ever documented pool of stolen credentials.
Unlike most other data breaches, this one wasn’t just the result of a single data dump. Instead, it was a compilation of over 30 separate batches of stolen data, most of which originated from infostealer malware, which means malware that silently harvests data from infected devices, browsers, and applications. Many of the leaked credentials came from prior leaks, although a significant portion appeared to be recent, actionable data. It’s worth noting that, unlike many past large-scale data breaches, this one was dominated by infostealer-acquired data rather than compromised cloud services.
Experts warned that this collection may turn out to be a “blueprint for mass exploitation,” paving the way for cybercriminals to launch automated credential stuffing, targeted phishing, and other large-scale forms of cyber fraud.
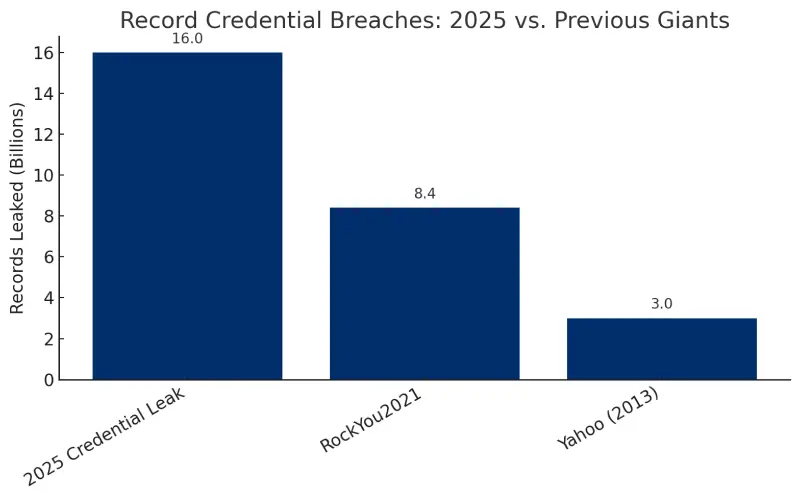
To get a sense of the scale of this year’s credential leaks, the second and third largest data breaches, RockYou2021 and Yahoo (2013), exposed 8.4 billion and 3 billion passwords, respectively, dwarfed by the 16 billion exposed in June 2025.
Debunking the 16 Billion Hype
Some critics have argued that the 16 billion headline number may be overstated, and that the dataset likely includes many duplicates, outdated credentials, and leaks from prior breaches. Analysts at infostealers.com described this breach as a “greatest hits” compilation rather than a single new breach.
Regardless, though, the consequences of this massive data breach are very real. This data dump includes countless fresh credentials stolen by recent infostealer malware, including high-value logins pulled from browser sessions, password managers, and auto-fill caches. Even older credentials can be highly effective in the hands of sophisticated cybercriminals, especially when combined with things like botnets and automation.
So, while the raw number may be inflated, the threat remains serious. Whether it’s one billion or sixteen, if your credentials are part of this compilation, you’re at risk. This isn’t marketing noise; it’s a credible threat that’s worth paying attention to.
Why Cloud-Stored Passwords Are at Risk
For most people, cloud-based password managers like LastPass and 1Password seem like a great option: Encrypted, accessible from anywhere, and convenient. But, as the scale of this recent breach shows, convenience can come with a price.
A single breach can cost you dearly
With a cloud password manager, all your login credentials are secured by a single master password. If this key is compromised, be it through phishing, malware, or surfacing in another breach, your entire digital life can be cracked wide open by an attacker.
This isn’t just a worst-case scenario, either. For instance, LastPass has suffered multiple breaches that affected customer vault data in the last few years, most recently in late 2022.
Reusing passwords puts you at risk
Password reuse is another common problem. It often feels like something that isn’t a huge deal, especially when the password you’re reusing is a secure one that hasn’t yet been exposed in a breach. But don’t fall into this line of thinking. No matter how secure your password is, all it takes is for it to be leaked once, and all your accounts that use that password will be at risk.
Cybercriminals use an automated process called credential stuffing to rapidly test all your accounts and see which ones you’ve reused the leaked password for. Your best bet is to simply never reuse a password, especially for high-value accounts like email, banking, or cloud storage.
Cloud syncing creates a new attack vector
Typically, cloud-stored passwords are automatically synced across devices. There’s no question this is convenient. But, this also means that if just one device in your ecosystem is infected with malware, such as an infostealer, your entire credential vault can be exposed without the cloud service being directly breached.
Even the most secure platforms can’t guarantee privacy
While most password managers encrypt your data, many cloud services retain access to your metadata, and sometimes, even your encryption keys. If the provider is compromised or legally forced to expose your credentials, for instance, through a subpoena, your login data could be out in the open without your knowledge.
Why SecureDrive and SecureUSB Are Safer Alternatives
Credential leaks are reaching unprecedented levels, and relying solely on cloud-based tools—even encrypted ones—is becoming an increasingly risky proposition. When your data is online, it’s inherently exposed to malicious attacks like stolen passwords, server-side exploits, or malware injected into your system.
SecureDrive® and SecureUSB® devices offer a fundamentally different approach that protects you from these risks: Encrypted, offline storage that you, and only you, physically control. Rather than relying on cloud-based solutions, these offline devices safely store your credentials, password manager exports, and two-factor recovery keys.
Both product ranges are built in a way that puts your security first, and come packed with features designed to keep your sensitive data protected:
- Military-grade hardware encryption: Your files are secured with AES 256-bit XTS encryption, regardless of your operating system or software.
- DriveSecurity™ antivirus protection: Each time a SecureDrive is connected, it automatically runs a built-in malware scan. This makes sure that your device is free of any credential-stealing malware like infostealers before any files can be accessed or transferred.
- Auto-lock and inactivity timeout: SecureUSB and SecureDrive devices automatically lock after a set period of inactivity, ensuring that your data can’t be accessed without your PIN or authentication method, even if you leave your device plugged in.
- No internet exposure: Since all your files are stored offline with SecureUSB and SecureDrive devices, there’s no remote login portal or cloud data centers for attackers to target.
With SecureDrive, you get large-capacity encrypted storage with enterprise-grade data and malware protection. With SecureUSB, you get the same encryption and data protection, packed into a compact, portable format ideal for people and teams that move around a lot.
Both options completely eliminate the risks tied to cloud syncing and browser-stored credentials, replacing them with something far more dependable: real-world security you can hold in your hand.
Best Practices for Protecting Your Credentials
When a breach of this scale happens, it’s a sobering reminder that good password hygiene isn’t optional; it’s essential. Whether you’re an individual user or a business handling sensitive client data, following best practices can go a long way toward protecting your passwords from being stolen or misused.
Here are a few essential steps to take:
- Use strong, unique passwords: Avoid reusing passwords across accounts. Instead, use long, randomly generated strings that include upper- and lower-case letters, numbers, and symbols. To add an extra layer of protection, store your passwords in encrypted offline backups using SecureUSB or SecureDrives.
- Enable two-factor authentication (2FA): 2FA adds an extra layer of security by requiring a second form of verification, making your accounts harder for an attacker to infiltrate. Where possible, opt for hardware-based 2FA (such as YubiKey or Google Titan) over text messages, which can be intercepted.
- Avoid browser-based password storage: Popular browsers like Chrome and Edge offer the ability to store your passwords, but using this feature makes them more vulnerable to credential-stealing malware. To maximize your security, disable this feature and instead use a dedicated non-cloud-based password manager.
- Be wary of phishing attacks: Phishing is still one of the most common methods by which credentials are stolen. Always double-check URLs, avoid clicking on suspicious links, and avoid entering login information into unfamiliar sites, no matter how legitimate they appear.
- Regularly audit your accounts: Tools like Have I Been Pwned are useful to stay up to date on whether your passwords have been exposed in a data breach. If you find that any of your passwords have been breached, change them immediately, and do the same for every platform where you might have reused them.
- Keep encrypted, offline copies of critical credentials: For your high-value accounts, it’s worth keeping an encrypted offline backup of your login credentials, especially if you rely on a cloud-based password manager. SecureUSB and SecureDrive are stand-out options for this, as they’re unmatched for both safety and portability.
Action Plan: What You Should Do Today
If you’ve read this post up to this point, you’re already ahead of most people. Your next step is to act on that awareness.
Here’s what you should do right now to safeguard yourself:
- Check if your credentials were exposed: Use a breach audit service like Cybernews Leaked Password Checker or Have I Been Pwned to see if any of your credentials have appeared in known breaches.
- Reset critical account passwords: Start with your most sensitive accounts: Email, banking, cloud storage, and work-related accounts. Use long, fully unique passwords for each one.
- Enable two-factor authentication (2FA) or passkeys: Where possible, turn on 2FA using an app or hardware key rather than text messages. If passkeys are supported, they’re an even better option, as they’re phishing-resistant and easier to manage.
- Adopt a trusted password manager: Use a reputable software-based password manager, or better yet, store your passwords in encrypted offline backups using bulletproof storage solutions like SecureUSB or SecureDrives.
- Store your credentials in secure, offline backups: Back up your credentials, recovery codes, and 2FA tokens on a hardware-encrypted device such as SecureDrive to prevent being locked out of your accounts in case of cloud service issues.
- Share what you know: Spread awareness with your team, family, or clients. Make sure they understand the risks of phishing, malware attacks, and weak password hygiene, as well as the importance of proactive security.
Stay Ahead of the Next Breach
The 16 billion credential leak is more than just a sensationalized headline—it’s a reminder that even the biggest platforms can’t guarantee the safety of your passwords. Cloud accounts, reused passwords, and weak security habits leave countless users vulnerable.
Fortunately, it’s not hard to change your habits and put your password security at the forefront of your mind. Good password hygiene, multi-factor authentication, encrypted backups, and hardware-based tools can go a long way toward protecting your accounts.d
For maximum peace of mind, SecureUSB and SecureDrive offer hardware-encrypted vaults for your credentials: Offline, secure, and always in your control.
Learn more about SecureUSB and SecureDrive for ultra-secure password storage and protect your data today!